In previous articles, we introduced readers to the concept of business continuity and its connection to cyberthreat. In this article, we explore another concept called Data Loss Prevention (DLP), which plays a crucial role in both cybersecurity and business continuity. DLP helps prevent the loss or leakage of critical organizational assets, directly impacting the security and continuity of business operations.
HIGHLIGHTS:
● An effective Data Loss Prevention (DLP) system is essential, as it safeguards sensitive information from leakage, mitigates risks, and ensures organizations can sustain secure and resilient business continuity. ● DLP (Data Loss Prevention) helps protect critical information, reduce cybersecurity risks, and support business continuity as well as organizational credibility. ● The operation DLP (Data Loss Prevention) encompasses data discovery and classification, policy definition, monitoring and control, as well as reporting and improvement. Altogether, these processes enable organizations to systematically and continuously prevent data leakage. ● DLP (Data Loss Prevention) is highly suitable for organizations managing sensitive information under stringent security or legal regulations, as it prevents data leakage and ensures resilient and secure business continuity. |
Understanding DLP
Data Loss Prevention (DLP) is a technology and process used to detect, prevent, and control the leakage of critical organizational information, including personally identifiable information (PII), financial data, customer information, or intellectual property. Therefore, DLP is a vital component of cybersecurity as it helps prevent data breaches, and it is also an essential element of business Continuity and risk management, as it reduces the impact of incidents that could disrupt business operations.
What makes DLP effective?
Implementing effective DLP technologies and strategies allows organizations to appropriately manage risks and ensure information security. An effective DLP system should include the following key features and components.
Covering all channels of data transfer.
● Monitor data in use, data in motion, and data at rest.
● Support multiple channels such as email, cloud storage, USB, and web upload.
Utilize precise detection technology.
● Content Inspection: Analyze the content of files, such as keywords or patterns (e.g., credit card numbers).
● Contextual Analysis : Consider the context, such as user, device, and location.
● Machine Learning / AI : Reduce false positives and adapt to real behaviors.
Integration with other systems.
● Integrates with SIEM, CASB, Endpoint Security, and Cloud Security.
● Supports operation in hybrid environments (On-premises + Cloud).
Well-defined policies and workflows.
● Define policies based on risks and compliance requirements such as GDPR and ISO 27001.
● Establish incident response workflows, including alerting, blocking, or encrypting data.
Support real-time operation and reporting.
● Instantly detect and block policy violations.
● Provide dashboards and reports for monitoring and auditing.
Scalability aligned with business expansion.
● Support organizational growth and cloud adoption.
● Continuous updates of threat intelligence and policies.
How is DLP important for organization ?
DLP (Data Loss Prevention) is highly important to organizations as it directly relates to information security, credibility, incident response, and business continuity. Its significance can be summarized into the following key points.
Protecting high-value information assets
● Information is a critical asset of the organization, such as customer data, financial information, and intellectual property.
● DLP helps prevent the leakage or loss of these data, which could otherwise cause enormous damage.
Mitigating Cybersecurity Risks
● Prevent data leakage from insider threats and external attacks.
● Minimize the chances of sensitive information being exploited in attacks such as social engineering or being sold on the Dark Web.
Compliance with laws and standards
● Helps organizations adhere to regulations such as GDPR, HIPAA, and ISO 27001.
● Reduces the risk of fines and lawsuits resulting from personal data breaches.
Maintaining organizational credibility and reputation
● Data breaches affect the trust of customers and business partners.
● DLP helps prevent incidents that could damage the organization’s reputation.
Enhancing Business Continuity and Cyber Resilience
● Reduce the impact of data loss incidents to ensure uninterrupted business operations.
● Work in conjunction with DRP and BCP to enable fast and secure system recovery.
What are the steps involved in the functioning of DLP?
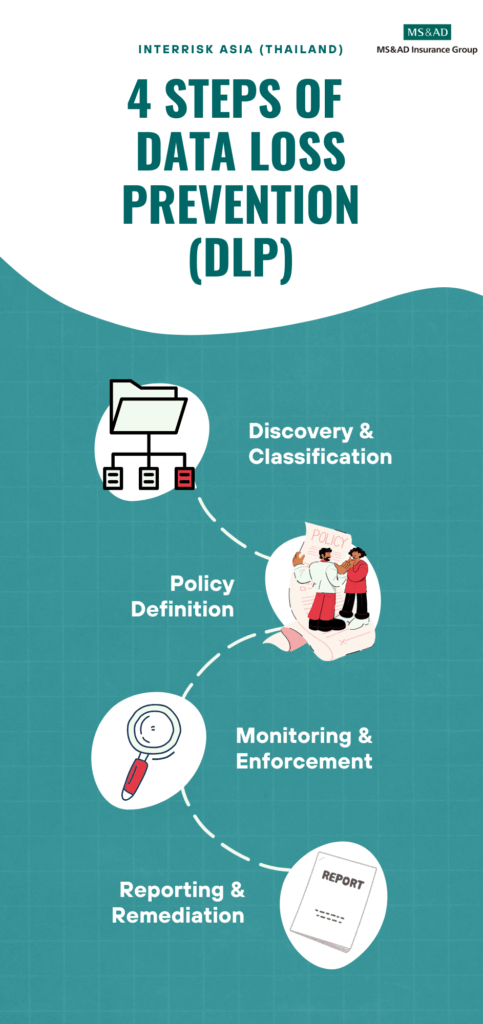
DLP typically operates through four key stages:
1. Discovery & Classification
- Verification and identification of sensitive information, including Personally Identifiable Information (PII), financial records, and intellectual property.
- Categorize data based on importance and risk to define appropriate policies.
2. Policy Definition
- Define governance rules for data usage and transfer, including restrictions such as preventing customer information from being sent via personal email or uploaded to unapproved cloud platforms.
3. Monitoring & Enforcement
- Monitor data usage in real time across Data in Use, Data in Motion, and Data at Rest
- Enforce policies such as blocking, encrypting, or alerting when violations are detected.
4. Reporting & Remediation
- Generate reports for monitoring and auditing purposes.
- Analyze incidents to improve policies and reduce false positives.
What types of organizations are suitable for DLP?
Data Loss Prevention is suitable for organizations that possess critical information and need to prevent data leakage, especially those with strict security and regulatory requirements, such as:
Organizations that handle Personally Identifiable Information (PII)
● Banks and financial institutions
● Insurance companies
● Government agencies that store citizen data
Organizations that handle medical data
● Hospitals and clinics
● Health insurance companies
● Required to comply with HIPAA or similar standards
Organizations with high levels of Intellectual Property
● Technology and software companies
● Industrial product manufacturers
● Research and Development (R&D) companies
Organizations required to comply with strict regulations
● GDPR (Europe), PDPA (Thailand), ISO 27001
● Companies working with global customer data
Organizations utilizing Cloud and Remote Work
● Data flows across diverse channels including email, cloud storage, and endpoint devices.
● Strict controls over data transfer are required.
Frequently Asked Questions (FAQs)
If the DLP system fails or a data breach occurs, what should an organization do?
Organizations should have a Business Continuity Plan (BCP) that outlines response procedures to incidents, such as using backup channels to control data, notifying relevant stakeholders, and conducting regular drills to ensure personnel can respond quickly and minimize business impact.
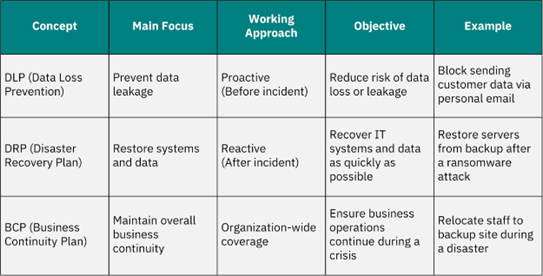
How is DLP different from DRP and BCP?
DLP (Data Loss Prevention), DRP (Disaster Recovery Plan), and BCP (Business Continuity Plan) are key components of Cyber Resilience. However, they have different objectives and scopes, as follows:
What are the main components or types of DLP?
The main components or types of DLP can be divided into three primary categories, based on where the data resides and how it is controlled: Network DLP, Endpoint DLP, Storage DLP
DLP is the key to Cyber Resilience and Business Continuity. InterRisk Asia Insight
Data Loss Prevention (DLP) is not merely a tool for preventing data leakage, but a critical component of Cybersecurity and Business Continuity. It helps reduce risks from threats, ensures regulatory compliance, and maintains organizational trust. In the digital era where data is a vital asset, investing in DLP is an investment in long-term business stability.
InterRisk Asia is a company specializing in comprehensive Risk Mangement,including Risk Assessment. Our services cover everything from consulting to develop BCM systems, to evaluating BCM effectiveness through detailed analysis with improvement recommendations, as well as training and Consulting across multiple industries. Operated by a team of consultants with direct experience in BCMS, we focus on designing plans tailored to the specific context of each business. We are committed to helping you build a holistic BCM plan — Turning Risks into Resilience together.
End-to-end consulting for the development of a robust BCMS, with pathways to ISO 22301 certification
Specialized training programs designed for both management and staff to enhance awareness and competency in BCMS practices.
Analysis of operational risks and disruption impacts to inform the development of targeted continuity strategies.
Structured exercises to validate your BCP and strengthen organizational preparedness and response capabilities.
Experienced consultants with hands-on BCMS expertise
Customized planning tailored to your business context.
Practical tools and templates, with expert support for testing and improvement.

